Case Study
LiveAction leverages QuestDB for AI-driven network security
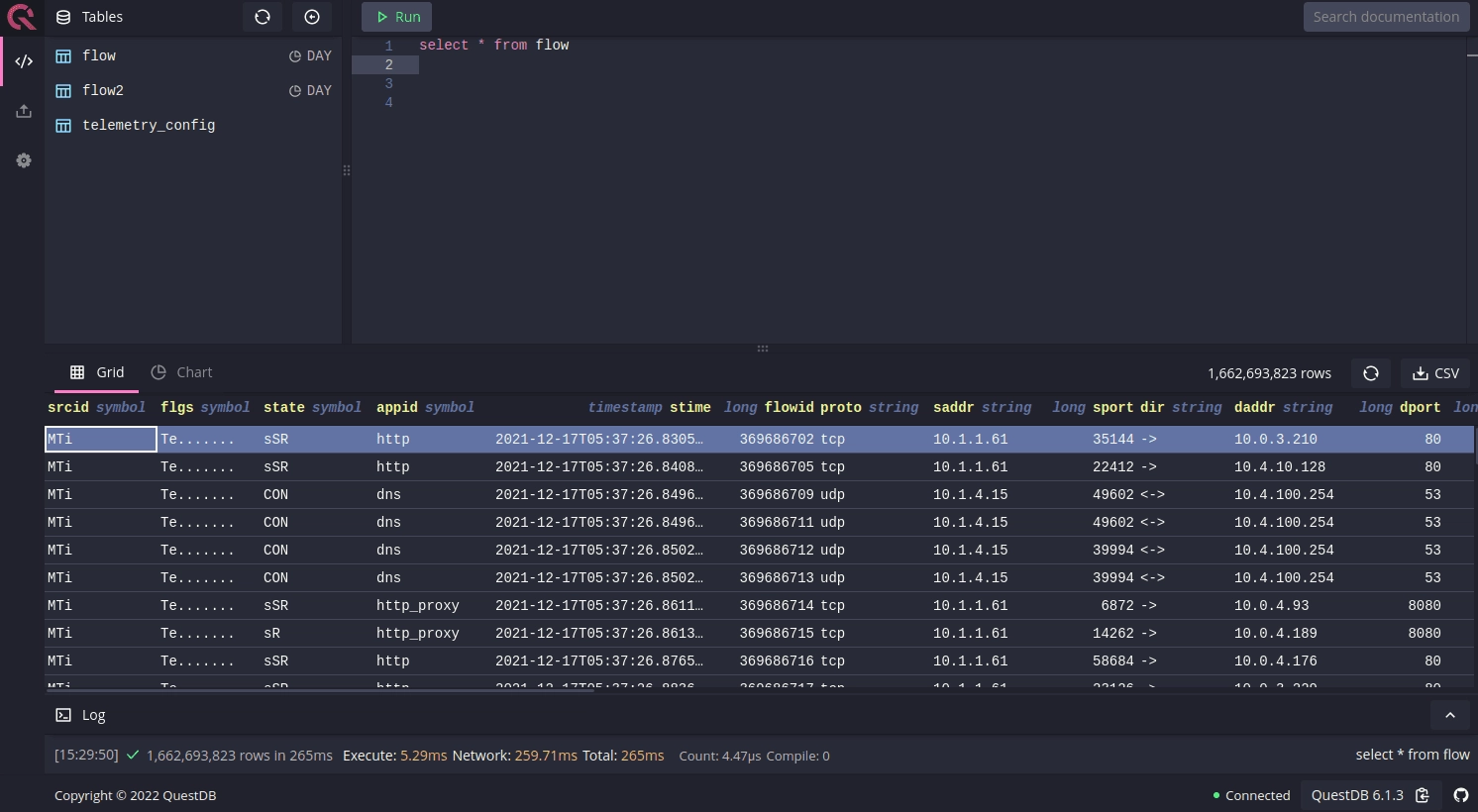
LiveAction uses QuestDB as a time-series database for storing massive traffic flow and encrypted traffic metadata. Afterwards, it facilitates efficient analysis of their real-time threat detection offering.
- Cost reduction
- QuestDB is efficient. Reduce resource consumption and better performance? Yes, please!
- RESTful API, and more
- QuestDB offers seamless integration with existing tech stacks.
- SQL compatibility
- Simple onboarding with time-series extended SQL for developers.

- Avg ingested rows/sec
- 3M+
- Write speed vs InfluxDB
- 10x
- Compression ratio
- 6x
- Cloud up-time
- 99.99999%
QuestDB enables threat detection
AI-driven network security
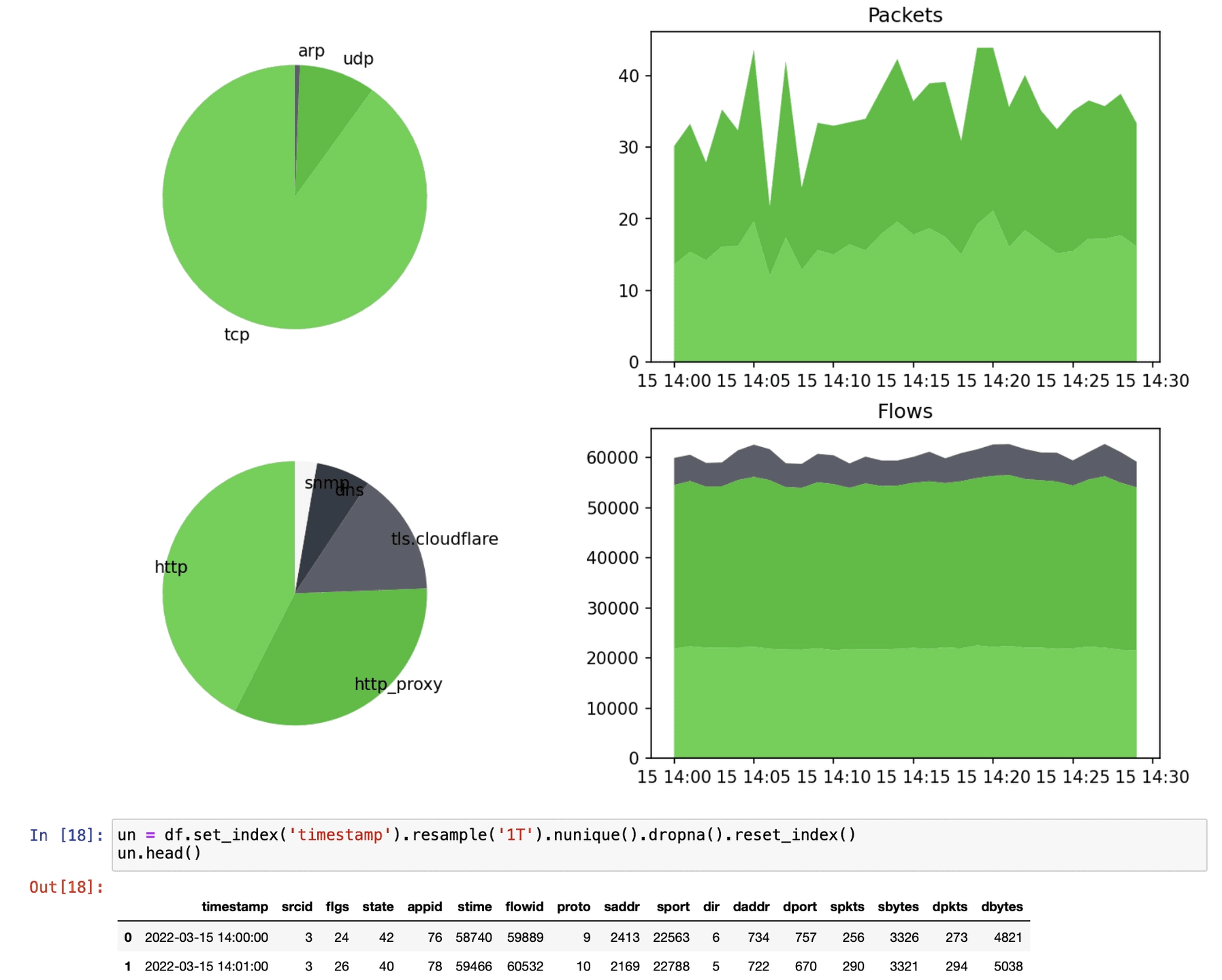
LiveAction integrates advanced security technologies into a streaming machine learning pipeline to identify network faults, anomalies, and threats in real-time. QuestDB keeps pace with massive volumes of traffic. Without the ballooning hardware requirements.
- Massive throughput analytics
- QuestDB handles millions of network events per second.

"QuestDB is impressive and stands out as a superior option. We use it as the basis of our time-series analytics for network threat detection."
Peak performance analytics
Network Threat Detection at scale
LiveAction leverages QuestDB's high throughput for efficient security analytics.
- Cost Reduction
- Better performance with less resource consumption.
- RESTful API
- Seamless integration with existing tech stacks.
- Clean data-in
- Deduplication, out-of-order indexing. Less cleaning, more insights.
Cutting-edge Network Security
QuestDB powers LiveAction's analytics
LiveAction relies on QuestDB for its high-throughput performance and seamless integration with their network security analytics. With native SQL support, QuestDB helps LiveAction detect network threats with ease.